Quick Tanks: The Best of Long-Form Defense Analysis, Briefly
A weekly review of the long-form content from the national security policy, defense policy, and related technology analysis community.
Happy New Year and welcome back, defense enthusiasts.
In this first installment of 2024, I have a suite of compelling reports for you all. Their topics are:
The various tradeoffs in designing space and airborne sensor architectures for missile defense
Russia’s critical vulnerabilities in the defense, economic, diplomatic, and political domains and how the West can exploit them
How to evolve US security cooperation approaches in an era of great power competition
Quick Tanks is a weekly collection and summary of the latest long-form analytic content on the topics of US defense, force structure, innovation, and policy considerations. We strive to aggregate all of the key sources of analysis and present brief, neutral summaries to help keep you informed. Should you feel inclined to learn more about any study, please reference the full report via the links provided.
The sponsor of the newsletter is the Hudson Institute’s Center for Defense Concepts + Technology.
Tank you for sharing and subscribing, and happy reading.
Getting on Track
Space and Airborne Sensors for Hypersonic Missile Defense
By Masao Dahlgren
Center for Strategic and International Studies
Link to PDF; Link to Report Page
Focus: The report focuses on the need for an advanced sensor architecture to detect, identify, and track missile threats.Analysis: The analysis draws on simulations, optimization studies, and modeling conducted by the CSIS Missile Defense Project to evaluate design tradeoffs in constellation design, assess coverage, and analyze sensor performance.Argument: Current missile defense capabilities are insufficient against modern missile threats, particularly hypersonic missiles. An effective architecture should be orbitally diverse, deploy sensors gracefully starting with regional coverage, and incorporate both space and airborne sensors.Insights: Proliferated low-earth orbit (LEO) constellations are vulnerable to systemic threats like space debris, cyber attacks, and nuclear detonations. Moreover, airborne sensors could provide useful regional coverage to complement space-based sensors. Importantly, as sensor architecture becomes more complex, the development of sensor fusion software is an underappreciated schedule risk.Recommendations: The report recommends a disciplined approach to acquiring the new sensor architecture, emphasizing the need for policy oversight to ensure schedule discipline, orbital and systems diversity, and adherence to missile defense requirements. Congress and the DoD should avoid temptations to optimize for coverage efficiencies at the expense of resilience and schedule. More specifically, they should explore persistent regional airborne sensors and accelerate investments into multi-sensor data fusion and common data standards to mitigate schedule risk.The proliferation of advanced ballistic and hypersonic missiles has heightened the urgency of developing an effective space sensor architecture for missile tracking and defense. As this CSIS report compellingly argues, “One cannot defend against what one cannot see.” Neither legacy warning systems nor surface radars can address emerging challenges like high-speed maneuvering weapons with unpredictable trajectories. Without robust space-based tracking, missile defense is fundamentally handicapped.
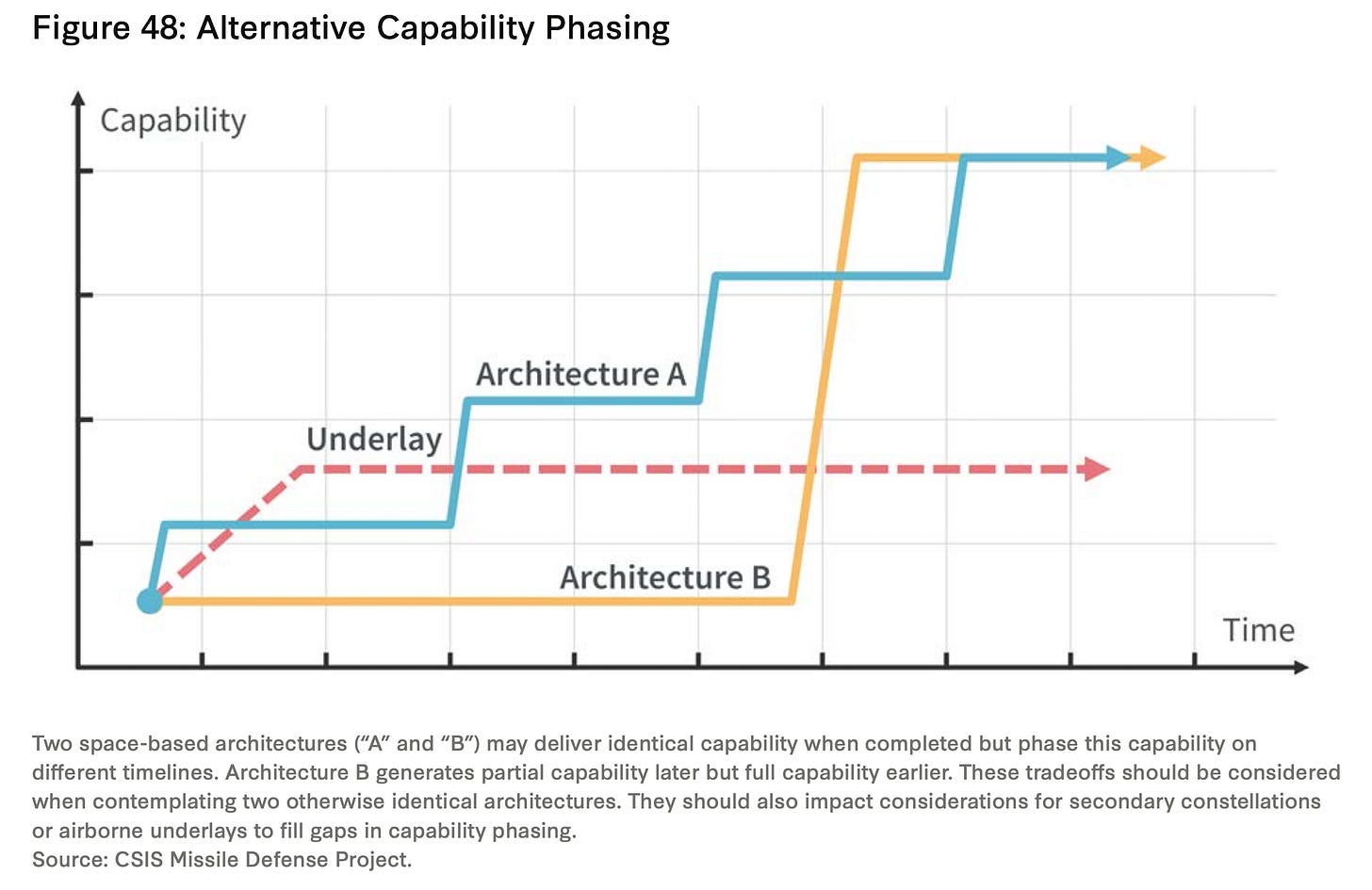
The report notes there is no perfect sensor architecture design. Rather, architects face complex trade-offs related to orbital regimes, sensor types and configurations that reflect policy assumptions and priorities. Each orbit offers advantages and disadvantages regarding coverage, cost, and resilience.
“LEO constellations benefit from proliferation and economies of scale but suffer challenges with persistence, orbital lifespan, and relative motion. MEO constellations offer more coverage and persistence but require potentially costlier satellites with larger apertures and radiation-hardened subsystems. GEO and HEO satellites provide unique coverage characteristics, requiring few satellites to selectively cover a given pole or longitude, but generate high unit costs and stringent reliability requirements. Airborne sensors can generate persistence unbounded by spacecraft orbital mechanics but have smaller detection footprints and require appropriate basing locations to operate.”
Likewise, sensor selection involves balancing factors like field-of-view, resolution, integration times, and fixed vs. mobile configurations. For one, wide field-of-view sensors can minimize the number of satellites needed but may sacrifice image resolution. Ultimately, the report argues a diversified architecture is prudent, leveraging multiple orbits and sensors so that adversaries must develop varied countermeasures.
As for the DoD’s current efforts, the author acknowledges several initiatives are underway. The planned Resilient Missile Warning/Missile Tracking (RMW/MT) constellation combines low and medium Earth orbit assets for complementary global coverage. In addition, the Hypersonic and Ballistic Tracking Space Sensor (HBTSS) and Next Generation Overhead Persistent Infrared (OPIR) represent significant steps in developing a comprehensive system for missile defense. With that being said, how these efforts are unified and scaled remains an open question.
Overall, the report identifies three main temptations in the development of sensor architecture that must be avoided. First, fire control missions enabling intercept guidance should not be abandoned despite technical hurdles. Secondly, constellations solely optimized for global sensor coverage risk delays fielding useful regional capability against priority threats. Finally, architectures consolidated into a single orbital regime invite disruption compared to diversified approaches.
The report incisively details the pressing need for elevated missile tracking, surveying available near-term technology options while clarifying longer-term pitfalls that could undermine this essential, emerging capability. I highly recommend reading the full analysis.
Identifying Russian Vulnerabilities and How to Leverage Them
By Andrea Kendall-Taylor, Richard Connolly, Siemon Wezeman, Gavin Wilde, Elina Ribakova, Benjamin Hilgenstock, Edward Fishman, Eric Ciaramella, Paul Stronski, Peter Schroeder, Timothy Frye and Maria Snegovaya
Center for a New American Security
Link to PDF; Link to Report Page
Focus: The report focuses on identifying critical vulnerabilities in Russia's defense, economic, diplomatic, and political domains after the invasion of Ukraine, aiming to inform US and allied strategies.Analysis: The report leverages a variety of data sources, including economic reports, defense industry analyses, and political assessments. It comprehensively examines Russia's dependencies on foreign technologies, economic sanctions impacts, military capabilities, and the state of its political and diplomatic relations.Argument: Russia has significant weaknesses across different areas that the West has not fully taken advantage of. By targeting these pressure points, the US and its allies can undermine Russia's capacity for aggression in Ukraine and beyond its borders.Insights: The exodus of IT professionals and reliance on foreign technology, especially for cybersecurity and military technology, signal a decline in Russia's technological self-sufficiency. Moreover, Russia's actions in Ukraine have strained relationships with key regions like Central Asia and the South Caucasus, diminishing its diplomatic influence. Thirdly, Russia's arms export industry is set to decline due to competition, the loss of key markets, and its inability to produce next-generation weapons.Recommendations: The US and its allies should tighten technology export controls to impact Russia's defense and cyber capabilities; strengthen sanctions, particularly in the financial and energy sectors; support Russian civil society and independent media to foster internal dissent; and deepen engagement with countries in Russia's periphery to reduce its regional influence.This CNAS report provides a comprehensive analysis of Russia's current vulnerabilities across various domains, crucial for understanding the national security landscape. By examining Russia's weaknesses in defense, economic, and political-diplomatic areas, the authors offer insights into how these vulnerabilities could be leveraged. Only through applying steady, forceful counterpressure against these fault lines can the West hope to roll back Russian aggression, facilitate gradual political change, and potentially enable more constructive relations with Russia.
The report first highlights several vulnerabilities in Russia's defense sector. These include a heavy reliance on imported components for weapon production, which makes Russia susceptible to supply restrictions. Additionally, the need to replenish its own arsenal and the impact of Western sanctions have complicated Russia's arms sales, a crucial revenue source. The report also notes the challenges faced by Russia's technology and cyber industries due to the loss of access to vital technology and talent, exacerbated by the war in Ukraine.
“Cyber power on the global stage draws from the interplay between state, commercial, human, and technical capacities. Russia now risks running major deficits in all these areas in the coming years. The private-sector ecosystem to develop and test new digital toolsets is now losing both institutional heft and investment capital. The domestic telecommunications infrastructure to both deploy and exfiltrate such toolsets is losing pace with global standards. Data storage capacity is reportedly at critically low levels, as is the country’s share of young, entrepreneurial, tech-savvy workers. R&D spending remains relatively stagnant. Russia has burned through a significant number of offensive cyber toolsets against Ukraine with little strategic impact—other than a much more resilient adversary—to show for it. Under such conditions, Moscow may be able to redirect dwindling digital and human resources toward the military and security services but will nonetheless have to run faster just to stay in place.”
Equally prominent are weaknesses in Russia’s undiversified, oil and gas-dependent economy which leaves national revenues vulnerable to sanctions pressure and fluctuations in global energy markets. Although high commodity prices buffered Russia in 2022, widening deficits and overreliance on its energy income stream spell trouble. Furthermore, Western sanctions and accompanying Russian capital controls continue to limit normal central bank operations and private sector access to foreign credit and investment. While Russia’s financial system has proven quite resilient so far, underlying issues remain that sanctions could still amplify.
“Ukraine’s sudden emergence as a soft power juggernaut also spells long-term trouble for Russia. Ukrainian activists have forced Russian musicians and performers who want to continue working in the West to denounce the war or else face a boycott. Ukrainian officials and athletes are cajoling the West into freezing Russian and Belarusian athletes out of international sporting competitions, especially the 2024 Olympics in Paris. Russian soft power was already on the decline before the invasion; Ukraine will make sure it is dead and buried.”
The report additionally calls attention to several mounting political and diplomatic vulnerabilities, highlighting the regime’s declining regional influence in Central Asia and the growing domestic discontent over the failures of the war effort. Russian diplomacy itself has become a liability rather than an asset, losing strength globally with reduced avenues to punch above the country's modest geopolitical weight. Lastly, Russia’s long-standing problem with ‘brain drain’ has intensified, as over 800,000 educated Russians have fled since the invasion, jeopardizing the country’s economic, technological, and military competitiveness.
While the report offers a range of recommendations, the overarching suggestion is for the United States and its allies to exploit these vulnerabilities strategically. This involves maintaining pressure on the defense industry, leveraging economic weaknesses, and taking advantage of political and diplomatic opportunities to reduce Russia's global influence and capability.
For a detailed understanding and a comprehensive view of these vulnerabilities and recommendations, I recommend reading the full report.
Winning the Future Together
Evolving Cooperative Security Approaches for Tomorrow’s Realities
By John T. Watts
Atlantic Council
Link to PDF; Link to Report Page
Focus: The report focuses on evolving US security cooperation approaches, particularly with its most capable allies and partners, to ensure they are more effective in an era of great power competition.Analysis: The report employs a qualitative analysis, drawing on discussions and workshops with a wide range of experts from industry, academia, and government.Argument: While the US security cooperation approach has been evolving, changes in the strategic context necessitate deeper reconceptualization to generate high-end cooperative security. The report argues for a more nuanced and flexible approach to cooperation, emphasizing the importance of aligning strategies with the specific needs and capabilities of different allies.Insights: The increasing importance of technological innovation in defense necessitates a shift from traditional military aid to more technology-focused collaborations. Secondly, the evolving nature of warfare, as evidenced in recent conflicts, highlights the need for dynamic and adaptable security strategies. Finally, interoperability in multinational defense efforts is critical to effectively leverage the strengths and capabilities of diverse allies.Recommendations: The report advocates for a "Collaboration-First" mentality with close and capable allies for effective information and technology sharing. It also emphasizes increasing cooperation in planning and production, as well as elevating the strategic prioritization and first principles planning of security cooperation activities. See below for the exhaustive list of recommendations.This Atlantic Council report examines how the United States can adapt its security cooperation approaches to ensure allies and partners are more capable and resilient amid intensifying great power competition. The author argues that while the core principles guiding US security cooperation remain sound, the modern threat landscape necessitates targeted evolutions in mentality, focus, and specific policies.
Considering Russia's invasion of Ukraine, the report explains how the prioritization of defense partnerships is now imperative, as the US and allies can no longer expend limited resources evenly across the globe. Meanwhile, Ukraine's effective absorption of advanced Western weaponry against Russia shows how emerging technologies can enable smaller forces to impose significant losses on more sophisticated adversaries. Thus, the modern threat landscape warrants careful reassessment of the roles, needs, and tools provided to allies.
The report also notes the major challenges to security cooperation in the 21st century. For one, insufficient stockpiles highlight the limitations in weapons production capacities across NATO states struggling to meet Ukraine’s requests. Moreover, the conflict in Ukraine is a reminder that adequate political will is necessary to access allies’ expansive arsenals. Indeed, while European allies actively assist Ukraine near their borders, few partners may deploy major assets to high-end fights distant from immediate interests. Thirdly, interoperability rests upon balancing cost and capacity, as exquisite US systems can be prohibitively expensive for allies. Fourthly, disconnects between US defense planning, force development, and security cooperation communities impede unified strategies. Lastly, allies now juggle intensifying economic ties with Russia and China against defense commitments to the US, creating complex political calculations amid multifaceted competition.
The report concludes with six major recommendations:
Embrace a ‘collaboration-first’ approach in information and technology sharing with key allies.
Expand pathways for adopting and adapting allied technological advancements.
Streamline processes like ITAR to remove counterproductive burdens and speed up foreign military sales (FMS).
Explore alternative means to fulfill partner capability needs, including co-production and integration of allied capabilities into U.S. systems.
Ensure security cooperation policy and strategic goal-setting is primarily threat-informed, considering partners' capability gaps and intentions.
Invest in and prioritize the security cooperation workforce, recognizing the importance of person-to-person relationships and strategic effects generated by security cooperation.
“To maximize the value of the network, DOD should take a ‘collaboration-first’ mentality with its closest and most capable allies in information and technology sharing. For example, rather than a reflexive move to classify documents as Not Releasable to Foreign Nationals (NOFORN) out of an over-abundance of caution or lack of proper training which unnecessarily constrains information-sharing with likeminded nations, DOD personnel should seek to be as collaborative as possible. While reforms are underway across DOD to improve issues of over-classification, these efforts must be broadened to encompass the way classification is taught, the mentality of leadership and desk officers, and even adjustments in simple systems, such as changing the order of drop-down classification options in digital interfaces so that NOFORN is not the top (and laziest) choice. The United States can also learn from its friends: In some allied nations, classification of information as NOFORN-equivalent requires approval by director and above leadership. Of course, this does not mean all information should be shared—or that classifications should be abandoned—rather it means that unnecessary barriers to information sharing ought to be further examined, and the mindset changed from a simplistic ‘better to be safe than sorry’ to considering what might opportunities or benefits might be lost by not sharing, and a realistic assessment of the actual risk of sharing.”
I highly recommend delving into the full report to further understand the analysis and recommendations.