Quick Tanks: The Best of Long-Form Defense Analysis, Briefly
A weekly review of the long-form content from the national security policy, defense policy, and related technology analysis community.
Welcome back, avid readers.
This week, I'm excited to present two enlightening reports for your consideration. They cover the following topics:
How "on-chip governance mechanisms" could allow for more effective and flexible governance of AI systems over time.
What are potential defense capabilities that can address the escalating challenge posed by China in the Western Pacific region
Quick Tanks is a weekly collection and summary of the latest long-form analytic content on the topics of US defense, force structure, innovation, and policy considerations. We strive to aggregate all of the key sources of analysis and present brief, neutral summaries to help keep you informed. Should you feel inclined to learn more about any study, please reference the full report via the links provided.
The sponsor of the newsletter is the Hudson Institute’s Center for Defense Concepts + Technology.
Tank you for sharing and subscribing, and happy reading.
Secure, Governable Chips
Using On-Chip Mechanisms to Manage National Security Risks from AI & Advanced Computing
By Onni Aarne, Tim Fist and Caleb Withers
Center for a New American Security
Link to PDF; Link to Report Page
Focus: The report focuses on the concept of "on-chip governance mechanisms" - technical restrictions and verification capabilities built into AI chips that could allow for more effective and flexible governance of AI systems over time.Analysis: The analysis revolves around the feasibility and implementation of on-chip governance mechanisms as a solution to AI governance challenges, relying on data and examples from current technology practices in companies like Apple and NVIDIA.Argument: On-chip mechanisms could enable more surgical, end-user-focused export controls for powerful AI chips, avoiding broad restrictions that harm US competitiveness. They also could support the verification of future multilateral agreements restricting the development of dangerous AI systems.Insights: On-chip governance mechanisms to enable adaptive governance in the AI domain, as new security regulations arise. Moreover, much of the needed functionality for on-chip governance is already in place in various chips, including cutting-edge AI chips. Thirdly, these mechanisms don't require invasive monitoring or insecure backdoors, but rather can be implemented through privacy-preserving verification and operating licenses.Recommendations: The report recommends a multi-faceted approach to implement on-chip governance. See below for the full list of recommendations.This timely CNAS report introduces the concept of "on-chip governance mechanisms" - secure physical mechanisms built directly into AI chips that provide a platform for adaptive governance of AI systems. As the national security risks from AI continue to rapidly evolve, flexible tools like this will be needed to effectively govern dual-use technologies without compromising American technological leadership.
The core of the article’s proposal is a hardened "security module" included on all high-performance data center AI chips. It relies on security features like secure boot, which verifies firmware integrity, and remote attestation, which uses digital signatures to authenticate measurements about the chip’s state. Specifically, remote attestation allows the module to securely verify claims about chip usage and location that can be trusted by a third-party regulator or manufacturer. For example, attestation could convey how much compute was used to train an AI model, without revealing proprietary code or data. Moreover, the module works in tandem with a timed operating license requiring periodic renewal. Failure to renew this license can remotely disable access to the GPU or other sensitive chip functions, providing an enforcement mechanism for policies. For instance, export-controlled chips could have their license revoked if end-use terms are violated. Importantly, many building blocks for these on-chip governance capabilities already exist on commercial chips from firms like NVIDIA, Apple, and Intel.
The report underscores how on-chip mechanisms allow more targeted controls regarding end-use, as compared to sweeping export regulations that risk "de-Americanizing" supply chains. This surgical approach reduces the need for broad, top-down bans while enabling policies like verifiably tracking the usage of AI chips. The existence of on-chip governance could also facilitate flexible international AI governance agreements in the future.
“Implementing these features on AI chips provides a platform for adaptive governance. These features would allow for a wide range of policies (for example, a training compute reporting requirement above a certain threshold, as called for by the recent White House executive order) to be implemented and updated directly on the chip by simply deploying a firmware or software update…These technical features ideally would be supported by robust supply chain tracking and “Know Your Customer” policies for AI chip exports/sales, which would allow the controller to know which chips are being used by which actors. This system of supply chain tracking also could include periodic monitoring and inspections to ensure that any novel attempts to physically tamper with chips can be caught.”
However, realizing the potential of on-chip governance requires ensuring these mechanisms reliably function even when adversaries actively attempt to circumvent them, such as in export control enforcement contexts. This necessitates hardening the security of existing technologies beyond their current commercial forms. The report advocates a staged approach to development and rollout that allows intermediate R&D to still serve production use cases. Initially, firmware updates could deploy basic operating license restrictions to exported AI chips, tying licenses to export terms. Subsequent generations would become tamper-evident, leaving indelible proof of physical tampering attempts. Finally, mechanisms would progress towards tamper-proofing on par with high-assurance hardware security modules. This gradual escalation in security allows on-chip governance to be tested and deployed in minimally adversarial settings while more mature tamper-resistance is developed for eventual application in openly adversarial contexts.
To achieve these goals, the report outlines several recommendations:
Establish government coordination: An executive order should be issued to create a NIST-led interagency working group focused on incorporating on-chip governance mechanisms into all export-controlled data center AI chips.
Create commercial incentives: The Department of Commerce should use advance export market commitments to incentivize US chip designers to conduct the necessary R&D.
Accelerate security R&D: NIST should coordinate with industry and government funding bodies to support R&D conducted outside leading chip companies, with a focus on technologies that would benefit from industry-wide standardization.
Plan for a staged rollout and extensive red-teaming: The Department of Commerce and the Department of Homeland Security should establish flexible export licensing and red-teaming programs to ensure the proper design and safe introduction of on-chip governance mechanisms.
Coordinate with allies: The State and Commerce Departments should work with allies on policies and standards for on-chip governance.
Encourage AI chip firms to move early: Chip firms should be motivated to build and harden the required security features for on-chip governance
I highly recommend reading the full report to better understand the technology behind on-chip governance and its potential implications.
Security in the Western Pacific
Building Future Capabilities in the Time of AUKUS
By Mark F. Cancian
Center for Strategic and International Studies
Link to PDF; Link to Report Page
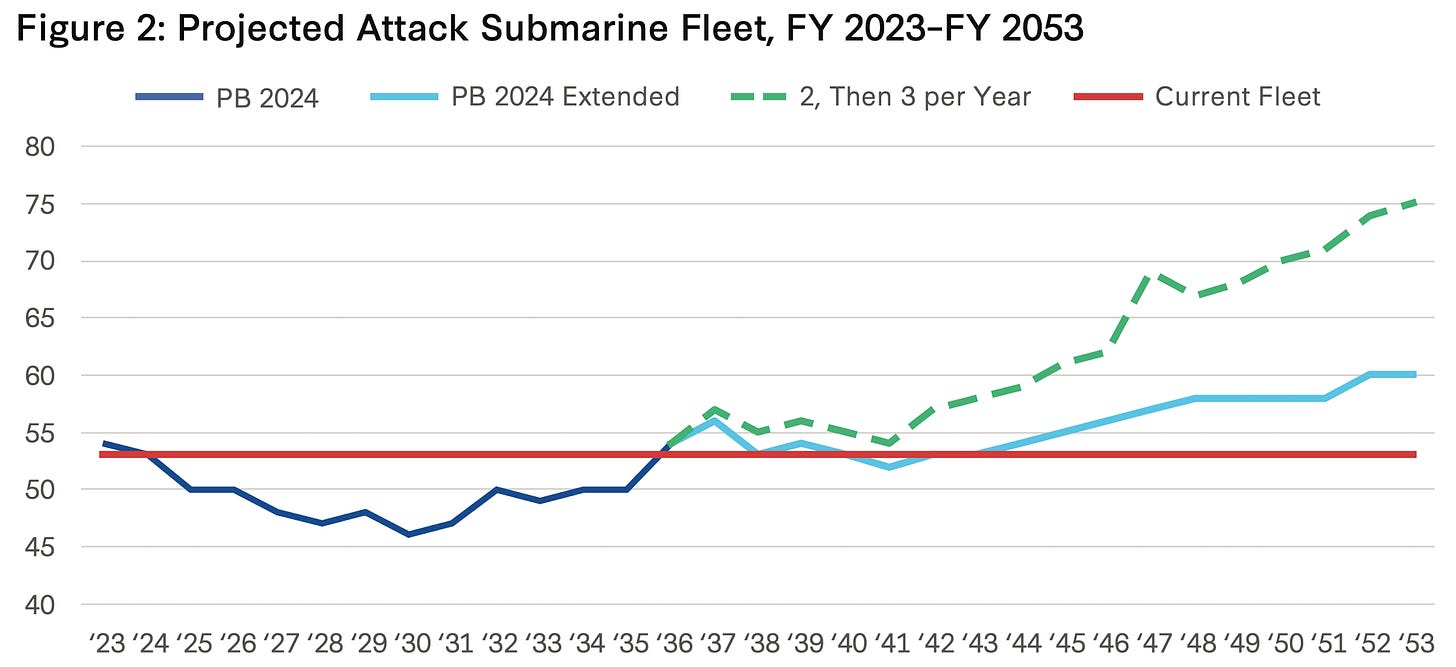
Focus: This report examines future defense capabilities needed to deal with the rising challenge from China in the Western Pacific, with a focus on the AUKUS agreement and its technology-sharing aims. Specifically, it looks at capabilities to pursue while waiting for an expanded submarine fleet, given constraints on submarine production.Analysis: The report analyzes wargaming scenarios related to a Chinese invasion, blockade, or gray zone campaign against Taiwan, as well as assessments of capabilities valuable in the Russia-Ukraine war. The report’s data sources include US Navy shipbuilding plans, proposed fleet architectures, and Congressional testimony.Argument: Although strategists want more attack submarines to compete with China, industrial base constraints mean the submarine fleet will decline through the 2030s before recovering. With the "submarine gap," the US and its allies need to explore other capabilities in the near/mid-term across various domains, such as large UUVs, electronic warfare, sea mines, aircraft hardening, and missile defense.Insights: AUKUS implementation faces barriers like export controls and data exchange restrictions that could hinder technology sharing. Moreover, with many potential avenues to pursue, industry needs signals on where to focus attention and resources.Recommendations: The author recommends governments and industry pursue a spectrum of capabilities that enhance submarine effectiveness, counter air threats, defend ships, and support allied interoperability. This includes large UUVs, upgraded missile defenses, advanced countermeasures, coalition training contractors, forward rearming, and hardened infrastructure. Ultimately, testing multiple approaches would reveal promising areas for further investment.As China continues its sizable military modernization evident in a naval fleet now larger than the US Navy and ground-based missiles that may outrange US systems, this CSIS report is critical for the defense industry and governments in identifying future capabilities to address the increasing challenge from China. It highlights the significance of the AUKUS agreement as a major development in this context. However, while strategists aim to expand submarine numbers, the current US fleet will not see substantial growth until the 2040s, necessitating alternative strategies to manage this gap. The report thus examines wargames and the Ukraine war to identify ways for the United States and its partners to address this challenge.
Wargames from CSIS, RAND, and CNAS reveal priority capability gaps the US and its allies must address to prevail in potential Western Pacific contingencies. Specifically, submarines boast unique survivability to strike behind enemy lines but lack the long-range missiles needed to fully capitalize on this advantage. Bombers can wield abundant standoff munitions yet remain acutely dependent on secure basing locations to even participate against Chinese missile barrages. Thirdly, uncrewed aerial and underwater platforms frustrate adversaries through dispersion and stealth, but they require supporting technologies and operational concepts optimized for Pacific distances.
Meanwhile, the Ukraine war spotlights additional deficiencies that demand urgent redress. Firstly, insufficient munitions quantities force difficult tradeoffs after months of supplying Ukraine has drained US inventories. In addition, atrophied industrial capacity precludes the surge production essential to wage the extended, intense war envisioned in a US-China conflict. Furthermore, the challenges in maintaining logistics under contested conditions call for innovative platforms and strategies to extend combat effectiveness, which is further complicated by gaps in interoperability among allies. Finally, deployable command systems and expanded training capacities must cultivate the coalition integration that any contingency spanning Australia to Japan would require.
Still, promising near and mid-term efforts can mitigate these shortfalls as the US and its allies await delayed expansions of attack submarine fleets. For one, uncrewed underwater vehicles would multiply manned submarines’ striking capacity inside Chinese defensive bubbles. Dispersed basing complicates targeting of what bombers remain in theater. Upgraded missile defense and electronic warfare tools enable surface ships and aircraft to operate at acceptable risk deeper into enemy battle networks. Essentially, collectively employing capabilities across domains, functions, and geographies accrues advantage to hedge against China’s military modernization until longer-range plans come to fruition.
The author notes further areas to explore including:
“Bring more forces to bear more effectively:
Deployable command, control, communications, and intelligence (C3I) packages would allow US forces to link more effectively with allies and partners.
Operational contracting can supplement limited military logistics units in providing the logistics needed to cover the vast expanses of the Pacific.
Plan to operate in a hostile environment:
Building hardened aircraft shelters would protect aircraft remaining at large bases during conflict.
Assisting Taiwan in developing a balanced force with both traditional and asymmetric capabilities would hedge against the spectrum of threats it faces, from gray zone harassment to invasion.
Hedge against unconventional threats:
Stronger countermine capabilities, long neglected by the U.S. Navy, would protect against a common adversary tactic.
Counter-swarming capabilities would allow military and civilian ships to continue operations without resorting to lethal force against harassing elements.
Defend against air threats in all their manifestations:
Expanding and fielding systems to counter adversary UASs would protect friendly forces from adversary reconnaissance and attack amid the ubiquity of such systems on the battlefield, and defensive systems against aircraft are generally too expensive for this use.
Think offensively, even when on the defensive:
Enhanced jamming and counter-C3I would disrupt China’s ability to coordinate forces.
Sea mines with standoff capabilities can emplace minefields with less risk to the launch platforms.
UASs can perform missions that are too dangerous, extended, or monotonous for crewed platforms.”
To better engage with the range of analysis on security in the Western Pacific, I urge you to read the full report.